
Telecommunications
Securing network infrastructure, subscriber identity, and cloud-native telecom systems
Industry Requirements
Modern telecom networks must meet stringent security, compliance, and performance standards:
Global Telecom
Compliance
Security modules must support FIPS 140-3, Common Criteria (e.g., AVA_VAN.5), ISO/IEC 27001, ETSI EN 303 645, and 3GPP/ETSI specifications. Alignment with GSMA guidelines is also critical for SIM/eSIM/iSIM and mobile security.
Performance and
Low Latency
Telecom platforms must sustain secure high-throughput encryption, message authentication, and key management with minimal power and processing overhead.
Advanced Attack
Resistance
Side-channel and fault injection attacks threaten telecom cryptographic implementations. Protection against DPA, CPA, EMA, and voltage/clock/EM glitching is essential to protect SIM provisioning, authentication, and key exchange.
Cross-Domain
Deployment
Security must extend from base stations and core networks to edge computing, public cloud platforms, and chiplet-based SoCs, including software fallback on legacy devices.
Long-Lived Cryptographic Protection
Telecom infrastructure, including satellites, base stations, and network hardware, often operates over decades and cannot be easily replaced or retrofitted. These long-lived assets must be protected today against tomorrow’s threats, including those posed by quantum computing. Security solutions must therefore offer post-quantum readiness and forward security to ensure confidentiality, authentication, and integrity throughout the full lifecycle of deployed systems.
Why FortifyIQ ?
FortifyIQ enables automotive platforms to resist real-world cyberattacks while meeting security, compliance, and performance goals.

Compliance-Ready – Designed to support FIPS 140-3 and SESIP (all levels), Common Criteria up to AVA_VAN.5, ISO/IEC 27001, ETSI, and GSMA-aligned guidelines.
What FortifyIQ Covers:
- Cryptographic solutions compliant with 3GPP security standards for mobile and fixed networks.
- Protection against physical attacks for communication devices and infrastructure.
- Support for secure key management, authentication, and OTAupdates.
- FIPS 140-3 L3/4, SESIP, and Common Criteria, including AVA_VAN.5 compliant cryptography modules.
Proven SCA/FIA resistance – Our hardware IPs are validated to meet and exceed certification benchmarks. AES (STORM) design carries formal proof of leakage-free operation. AES (RAMBAM) implementation is validated to over 1 billion traces in simulation and on an FPGA board and is Common Criteria AVA_VAN.5 validated. HMAC SHA2 implementations are validated in simulation and on an FPGA board to over 100 million traces. ECC/RSA is validated in silicon to X million traces. Our software libraries are validated past 100 thousand traces, meeting top tier security regulations.
Optimized for telecom needs – Crypto cores meet real-time, power-sensitive constraints typical of base stations, secure elements, and edge infrastructure.
AI Post-quantum readiness – FortifyIQ supports AES, HMAC, and classical PKA (ECC/RSA), as well as ML-KEM and ML-DSA post-quantum cryptographic cores, providing long-life cryptography support, particularly crucial for satellites and infrastructure.
Ultra-flexible deployment – Solutions available as software, soft IP, or RoT modules, easily integrated into virtualized platforms, Caliptra- or OpenTitan-based architectures, or telecom chiplets. Our solutions are implementation-, technical- and foundry-agnostic.
Security Boutique – We tailor performance-class crypto, interfaces, and protections to your RAN/core/edge architecture, and support optimization and integration changes through the entire design cycle up to tape-out.
Security Validation and Cryptographic Assurance.
FortifyIQ’s cryptographic IP cores, built on mathematically and practically validated countermeasures, ensure robust protection against advanced physical threats.
AES IP cores include:
- RAMBAM: Validated to AVA_VAN.5 by SGS Brightsight. TVLA-compliant with over 1 billion trace validations, meeting and exceeding regulatory standards.
- STORM: Formally proven side-channel security with minimal silicon footprint. TVLA-validated on over 15 million traces.
HMAC-SHA2 IP cores include:
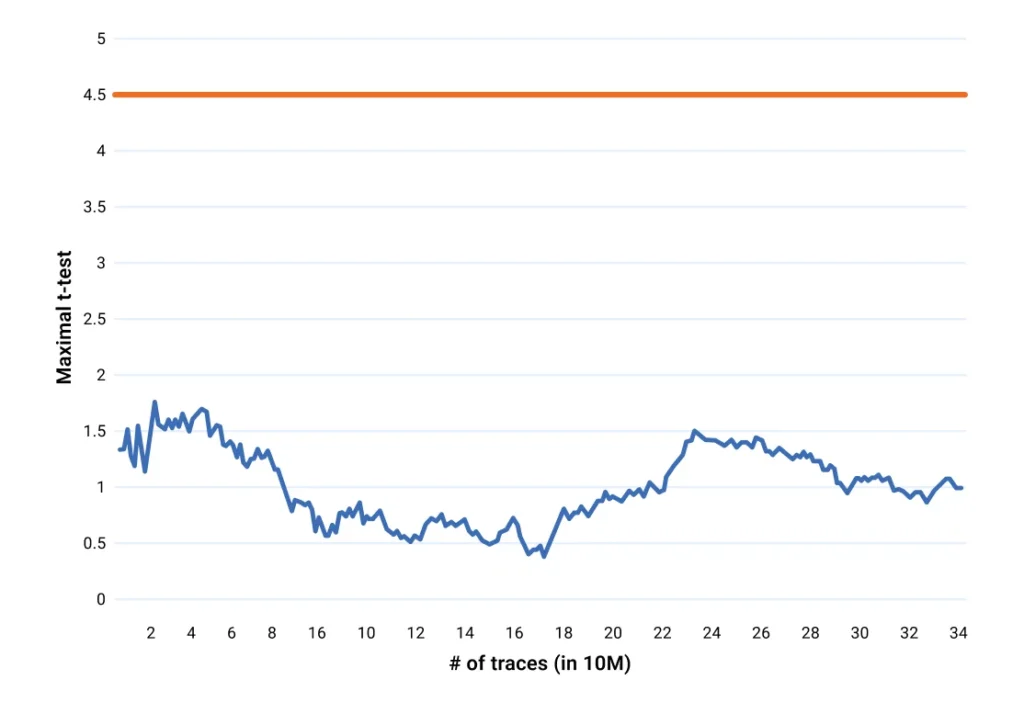
- HMAC-SHA2: Based on a patented variant of the security-proven Threshold Implementation (TI), validated to meet the highest cryptographic regulatory standards (and TVLAvalidated on over 100 million traces).
- Compact-Fast HMAC-SHA2: Validated to 100 million traces against the known attacks. The diagrams show that the attack succeeds on the unprotected version, vs on our protected version, where it will clearly never succeed.
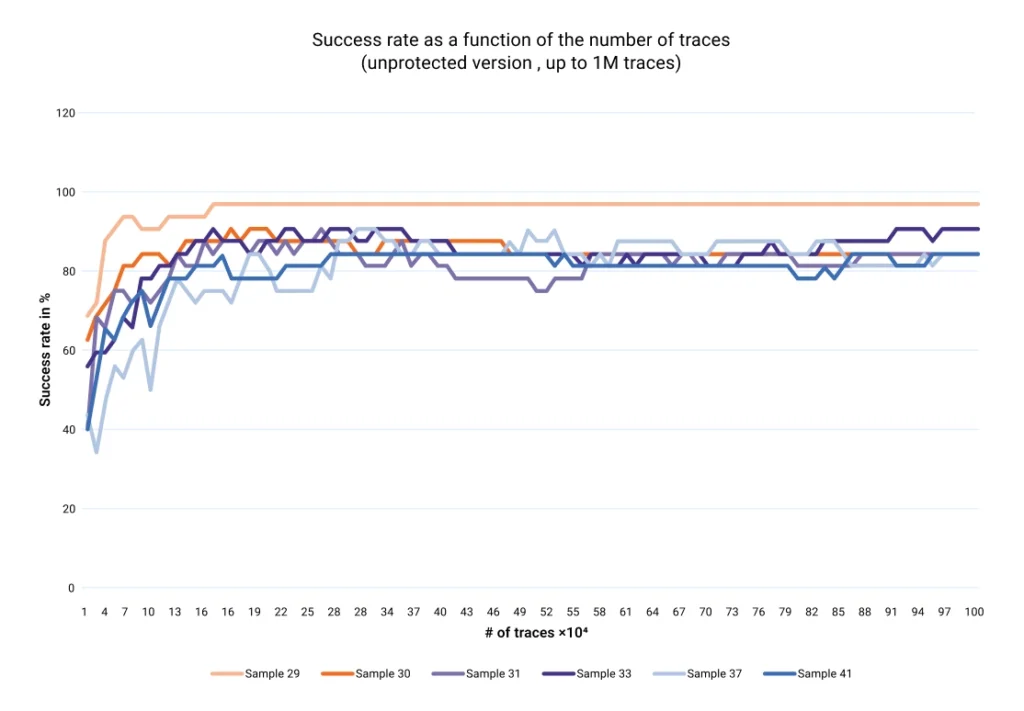
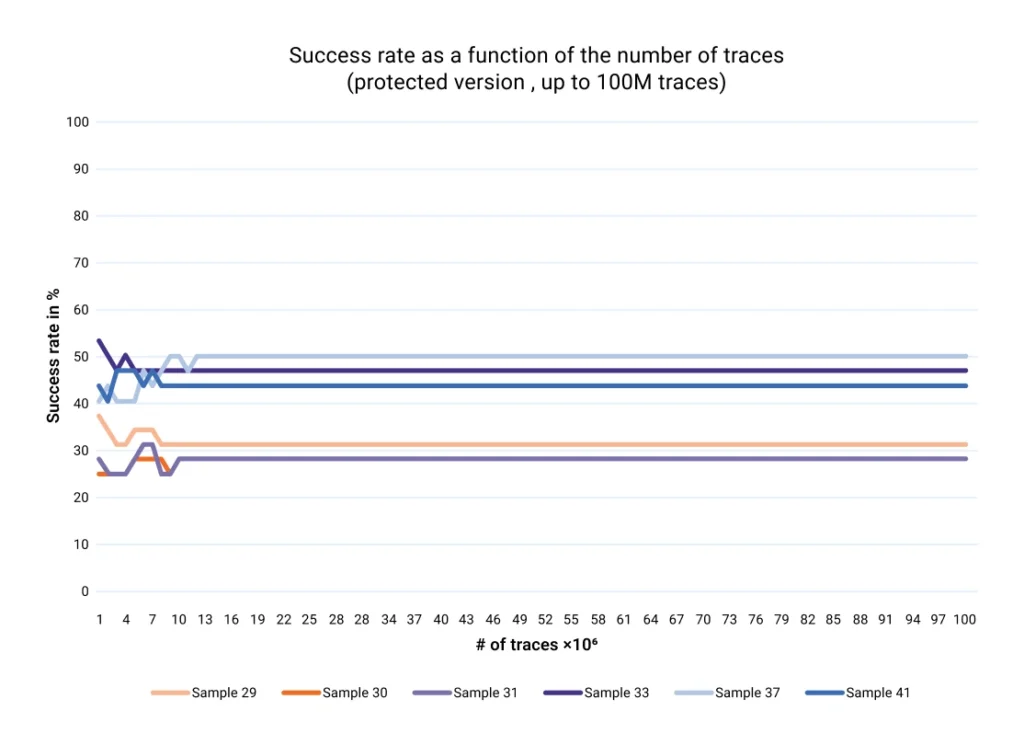
Our validation methodology includes:
- Pre-silicon RTL validation using FortifyIQ’s EDA tools (TVLA, gate-level trace, attack simulation)
- FPGA and silicon post-silicon testing
- Protection against DPA, CPA, EMA, and fault injection (voltage, EM, clock)
- Optional detection of non-invasive fault injection
- After release, when relevant, our IP cores are validated and/or certified by third-party labs either as standalone blocks or integrated into complete secure chips.
Documentation provided for compliance under FIPS 140-3, Common Criteria, and telecom-aligned international standards.

Applications
and Use Cases
FortifyIQ supports telecom operators, infrastructure vendors, and chip designers across the full spectrum of telecom deployment:
SIM/eSIM/iSIM Provisioning
Protect key storage, personalization, and provisioning with validated AES and HMAC SHA2 cores and RoT support. Software libraries offer fallback options for legacy provisioning.
Subscriber Authentication and Session Integrity
Secure cryptographic primitives used in AKA, NAS, RRC, MACSec, IPsec, and TLS layers with post-quantum readiness and proven protection against leakage and injection.
Telecom Cloud and Edge Computing
FortifyIQ crypto IP and software protect workloads in virtualized, containerized, and edge-hosted environments where physical control is limited.
Virtualized Network Functions (VNFs) and SDN Platforms
Ensure isolation, key protection, and authenticated control messages with software and hardware crypto resistant to real-world attacks.
5G Base Stations and Network Equipment
Harden SoC-based baseband processors and secure elements with FortifyIQ IP, meeting stringent latency and power, performance and area targets while resisting physical attacks.
OTA Firmware and Software Updates
RoT modules ensure firmware authentication and secure boot, including over-the-air provisioning on vulnerable baseband and control platforms.
Critical Communications and Private Networks
Secure public safety and industrial telecom environments with AES, HMAC, and RoT components that deliver high assurance under resource and compliance constraints.

FortifyIQ
Solutions for
Telecom Systems
Solution Category
FortifyIQ Offering
FortifyIQ Offering
AES, HMAC-SHA2, ECC, RSA, etc., and PQC, SCA/FIA-resistant software libraries for mobile CPUs, edge devices, and secure fallback.
FortifyIQ Offering
Side-channel and fault-resistant AES, HMAC, ECC/RSA, and PQC IPs with industry-leading power, performance, and area (PPA) and compliance-ready validation.
FortifyIQ Offering
Secure anchors enabling verified boot, key management, and in-line encryption in chiplet-based and telecom-grade SoCs.
FortifyIQ Offering
RTL-level simulation and attack validation tools for SCA/FIA resistance, used internally and by telecom hardware designers.
Let's Secure the Future of
Telecommunications Systems
FortifyIQ safeguards network infrastructure, subscriber identities, and cloud-native telecom systems.