Defense and Aerospace: Mission-Critical Security at Every Altitude
Protecting secure communications, critical systems, and advanced AI with certified resistance to physical attacks
The Defense and Aerospace sectors demand cryptographic solutions that are certifiable, tamper-resistant, and future-proof, capable of protecting everything from secure field radios and satellites to AI-based targeting and avionics control systems. These systems often operate in adversarial environments where physical access, side-channel attacks (SCA), and fault injection (FIA) are real threats.
FortifyIQ delivers software and hardware cryptographic solutions designed to meet the highest levels of assurance, for both newly developed systems and deployed platforms needing secure upgrades. Our hardened cryptographic IP cores, software libraries, roots of trust, and EDA tools are engineered to secure mission-critical data across air, land, sea, space, and cyber domains.
The Security Challenges in
Defense and Aerospace
Real-World Adversaries
Devices are often deployed in contested environments and must remain secure even when physically captured or tampered with, protecting keys, algorithms, and mission data.
Legacy Systems in Need of Modern Protections
Military and aerospace platforms are often expected to remain in use for decades. Many have no hardware security features, yet must meet today’s strict cryptographic assurance levels. OTA upgradable, physically hardened software libraries are one of the only viable ways to retrofit secure cryptography into legacy equipment.
Secure AI and ML at the Edge
From autonomous drones to radar systems and tactical AI engines, AI must be protected against model theft, inference manipulation, and reverse engineering. FortifyIQ's EDA tools and crypto IPs defend AI models against physical extraction and runtime compromise.
Post-Quantum Threats
Nation-state adversaries are preparing for the quantum era. Cryptographic systems in defense must be quantum-safe now, and hardened against both algorithmic and physical threats.
Compliance and Certification
Defense systems must meet a range of international and national security standards, including:
- FIPS 140-3 Levels 3/4 (cryptographic modules)
- Common Criteria AVA_VAN.5 (resistance to physical attack)
- NSA Commercial Solutions for Classified (CSfC)
- DO-326A / DO-356A for aviation cybersecurity
- NATO, NIST, and EU NIS2 guidance
Why FortifyIQ ?
FortifyIQ delivers hardened cryptographic IP, software, and EDA tools designed to meet the mission-critical security, integration, and compliance demands of aerospace and defense platforms, including radiation tolerance. Side-channel and fault injection protection for industry-specific applications, can also be provided by request.

Delivered as soft macros (synthesizable RTL), portable across ASICs, FPGAs, and mixed-technology platforms
Technology-, implementation-, and foundry-agnostic, our algorithmic cryptographic protection applies equally in any silicon process or system architecture
No custom instructions or nonstandard integration paths: FortifyIQ crypto cores integrate like any standard cryptography IP core
Defense-grade secure boot and attestation, with hardened Roots of Trust and crypto cores for trusted computing environments, optimized for minimal latency and area, designed for constrained platforms like field radios and tactical drones
PQC support for long-lifecycle threat protection, including ML-KEM and ML-DSA for future-proofed defense applications
For In-House Development, FortifyIQ’s Pre- and Post-Silicon Validation Tools, Side-Channel Studio and Fault Injection Studio, help eliminate vulnerabilities before deployment. These EDA tools validate physical attack resistance across execution timing, routing, memory, and submodules.
Security Boutique: we tailor countermeasures, interfaces, and crypto configurations to your space platforms, with deep customization and architectural flexibility up to tape-out.
Rigorous Validation Assurance: FortifyIQ cryptographic IP cores, built on mathematically and practically validated countermeasures, ensure robust protection against advanced physical threats.
AES IP cores include:
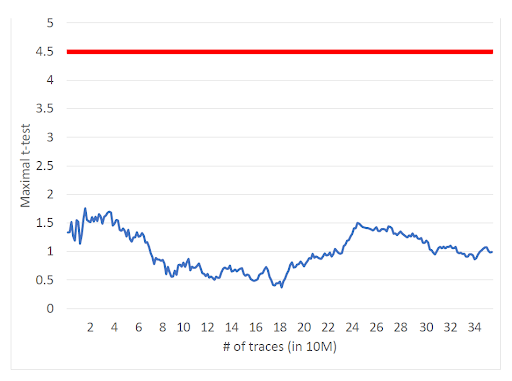
- STORM: Formally proven side-channel security with minimal power consumption. TVLAvalidated against over 15 million trace validations. See the STORM scheme’s security proof here.
HMAC-SHA2 IP cores include:
- HMAC-SHA2: Based on a patented variant of the security-proven Threshold Implementation (TI), validated to meet the highest cryptographic regulatory standards (and TVLAvalidated on over 100 million traces).
- Compact-Fast HMAC-SHA2: Validated to 100 million traces against the known attacks.
Our validation methodology includes:
- Pre-silicon RTL validation using FortifyIQ’s EDA tools (TVLA, gate-level trace, attack simulation)
- FPGA and post-silicon testing
- Protection against DPA, CPA, EMA, and fault injection (e.g. voltage, EM, clock)
- Detection of non-invasive fault injection
After release, and when relevant, our IP cores are validated and/or certified by third-party labs either as standalone blocks or integrated in complete secure chips.
FortifyIQ Security Solutions for Defense and Aerospace
Pre- & Post-Silicon
Validation Tools
For semiconductor teams building aerospace-grade chips:
- Identify side-channel and fault injection vulnerabilities before tapeout
- Integrates smoothly into the functional verification workflow, using the same testbench
- Validate SCA/FIA resistance post-silicon
- Demonstrated on cryptographic modules and embedded AI accelerators
Software Crypto Libraries
For devices without hardware protection:
- AES-256, HMAC-SHA-512, ECC/RSA, all hardened against SCA and FIA, and security certifiable
- Post-quantum cryptography (PQC) libraries in advanced development
- Runs on resource-constrained MCUs and MPUs, even in legacy avionics
- OTA-upgradable, processor-agnostic, certification-ready

Hardware Crypto IP Cores
For high-assurance embedded designs:
- SCA/FIA-hardenedAES, HMAC, ECC/RSA, and PQC
- Optimized for exceptional power, performance, and area (PPA)
- Integrates with FPGAs, secure MCUs, and SoCs, (for satellites, drones, avionics, etc.)
- Radiation Tolerance available on request
Root of Trust & Cryptobox IPs
For embedded lifecycle security:
- Compact roots of trust for secure boot, firmware updates, and mission data protection
- Cryptobox IPs integrate any combination of AES, ECC/RSA, PQC, and HMAC in one hardened subsystem
- Designed for constrained and latency-sensitive platforms like UAVs and field comms
- Application-specific SIA/FI protections by request for your defense and aerospace applications

Use Cases:
Securing Defense and Aerospace Systems
Military Radios & Tactical Edge Devices
Prevent key leakage, secure OTA updates, and protect embedded AI logic
Drones & UAVs
Secure flight software, control channels, and real-time AI inference
Satellites & Spacecraft
Deploy crypto hardened against physical attack and radiation exposure
Classified Communications
Align with NSA and NATO cryptographic guidelines
Avionics Systems
Meet DO-326A/DO-356A mandates and protect avionics from tampering
Radar, C4ISR & Targeting AI
Prevent model theft and ensure integrity of mission-critical inference and control
FortifyIQ Supports Defense Industry Standards:
- Cryptographic IP and software aligning with FIPS 140-3 Levels 3/4, Common Criteria AVA_VAN.5, and NSA Suite B cryptography.
- Solutions designed for classified communication, avionics, and embedded AI security.
- Support for DO-326A / DO-356A aviation cybersecurity standards.

Certifiable, Deployable, Future-Proof