FortiPKA-RISC-V
Secure, Swift and Versatile
Description
Modern asymmetric cryptography algorithms such as RSA or elliptic curve cryptography over prime fields require complex mathematical calculations of large numbers up to 4096 bits. FortiPKA-RISC-V is a public key accelerator that allows offloading all the computationally heavy operations from the main CPU, while offering excellent balance between small footprint and high performance.
One of the key features of FortiPKA-RISC-V is a unique computation technology that eliminates the necessity for data transformations to and from the Montgomery domain, which leads to superior performance compared to alternative solutions. The efficient resource usage is ensured by implementation of cryptographic algorithms in firmware that is executed on an internal miniature RISC-V core. The core instruction set is extended to support custom modular arithmetic for large integers. Hardware configuration options are available to balance area and performance for specific applications. Moreover, FortiPKA-RISC-V supports CPU interfacing through AMBA AXI4, APB, AHB or custom memory-like slave interface.
To ensure smooth integration of FortiPKA-RISC-V to a customer’s product, a software library which performs high-level operations, such as encryption, decryption, signing and verifying for a variety of cryptographic algorithms is provided. Supported algorithms include RSA, DH, DSA, ECDH, ECDHE, ECDSA, EdDSA, DH and SM2. Additionally, FortiPKA-RISC-V’s technology-agnostic design ensures compatibility across diverse semiconductor technologies.
FortiPKA-RISC-V includes all the necessary countermeasures against modern side-channel and fault injection attacks. The protection level is configurable, allowing to further improve security characteristics at the cost of resource usage or computation speed. To minimize the overhead of protections from physical attacks, countermeasures are employed in hardware, firmware and software when appropriate.
Deliverables
- SystemVerilog source code or netlist
- Testbench, input vectors and expected results
- Sample timing constraints, synthesis and simulation scripts
- Hardware Abstraction Layer (HAL) reference implementation
- Integration, configuration and usage manuals
- Firmware code
- Software library
Tech Specs
- Part Number
FIQPKA-RISC-V-IP
- Short description
Public Key Accelerator
- Provider
FortifyIQ, Inc.
- Foundry, Node
Independent
- FPGA
AMD Xilinx, Intel, Lattice
- Maturity
—
- Compliant standard
ANSI X9.31, ANSI X9.42, ANSI X9.62, ANSI X9.63, PKCS#1, IEEE Std. 1363-2000, AIS-31, FIPS 140-2, FIPS 186-3
- Availability
Available
- FPGA Technology
—
- TSMC
—
Applications
- Networks
- Communications
- Payment Systems
- Authentication Devices
- IoT Devices
- Embedded Systems
Request This Core
Features
The performance/area metrics can vary depending on the specific configuration, interface, and chosen standard cell library.
- Modular exponentiation operations with up to 4096-bit modulus
- Prime field ECC operations with up to 571-bit modulus
- Fastest implementation is 58 kGE and 68 Op/s for 2048-bit RSA, 431 Op/s for 1024-bit RSA, 150 Op/s for 384-bit scalar multiplication
- Smallest implementation is 33 kGE and 67 Op/s for 1024-bit RSA, 24 Op/s for 384-bit scalar multiplication
- Up to 350 MHz on the 45 nm process
- Unique mathematical solution that eliminates the need for preprocessing
- Software library with support for RSA, DH, DSA, ECDH, ECDHE, ECDSA, EdDSA, DH, SM2
- CPU interface support for AMBA AXI4, APB, AHB and custom memory-like slave interface
- RAM and ROM option for firmware storage
- Strong protection against modern side-channel and timing attacks, and fault injection attacks, tunable security level
- Technology agnostic
- Native support for standard NIST curves, optional support for custom curves
- Shared memories between host CPU and FortiPKA-RISC-V that enables memory reuse
- High level of customization on software, firmware and hardware level
Benefits
- Enhanced performance with no need for data preprocessing
- Optimal balance between high performance and low area
- Robust defense against side-channel and fault injection attacks, with customizable options to meet diverse cryptographic requirements
- Hardware configuration options allowing to optimize FortiPKA-RISC-V for specific applications
- Versatile CPU Interfaces: AMBA AXI4, APB, AHB, or a custom memory-like slave interface
- Extensive Algorithm Support: RSA, DH, DSA, ECDH, ECDHE, ECDSA, EdDSA, DH, and SM2
- Facilitation of memory reuse due to shared memory resources
- Seamless integration into customer products, supported by a comprehensive set of deliverables and documentation
Number of cycles per operation
Bits | Fastest | Optimal | Smallest | |
Modular | 4096 | 4 309 | 16 805 | 132 422 |
2048 | 1 133 | 4 309 | 33 446 | |
Modular | 4096 | 131 | 259 | 515 |
2048 | 67 | 131 | 259 | |
EC point | 521 | 2 207 | 5 951 | 36 539 |
256 | 618 | 1 581 | 9 282 | |
EC point | 521 | 2 001 | 5 293 | 31 897 |
256 | 576 | 1 433 | 8 152 | |
Modular | 4096 | 10 345 240 | 37 186 042 | 283 136 955 |
2048 | 1 617 316 | 5 181 774 | 37 344 415 | |
1024 | 315 179 | 812 521 | 5 201 122 | |
Scalar | 521 | 2 469 613 | 6 195 165 | 37 411 457 |
384 | 908 377 | 2 337 101 | 14 326 683 | |
256 | 371 773 | 850 693 | 4 576 683 |
Operations per second, 350 MHz
Bits | Fastest | Optimal | Smallest | |
Modular | 4096 | 81 225 | 20 827 | 2 643 |
2048 | 308 914 | 81 225 | 10 465 | |
Modular | 4096 | 2 671 756 | 1 351 351 | 679 612 |
2048 | 5 223 881 | 2 671 756 | 1 351 351 | |
EC point | 521 | 158 586 | 58 814 | 9 579 |
256 | 566 343 | 221 379 | 37 707 | |
EC point | 521 | 174 913 | 66 125 | 10 973 |
256 | 607 639 | 244 243 | 42 934 | |
Modular | 4096 | 34 | 9 | 1 |
2048 | 216 | 68 | 9 | |
1024 | 1 110 | 431 | 67 | |
Scalar | 521 | 142 | 56 | 9 |
384 | 385 | 150 | 24 | |
256 | 941 | 411 | 76 |
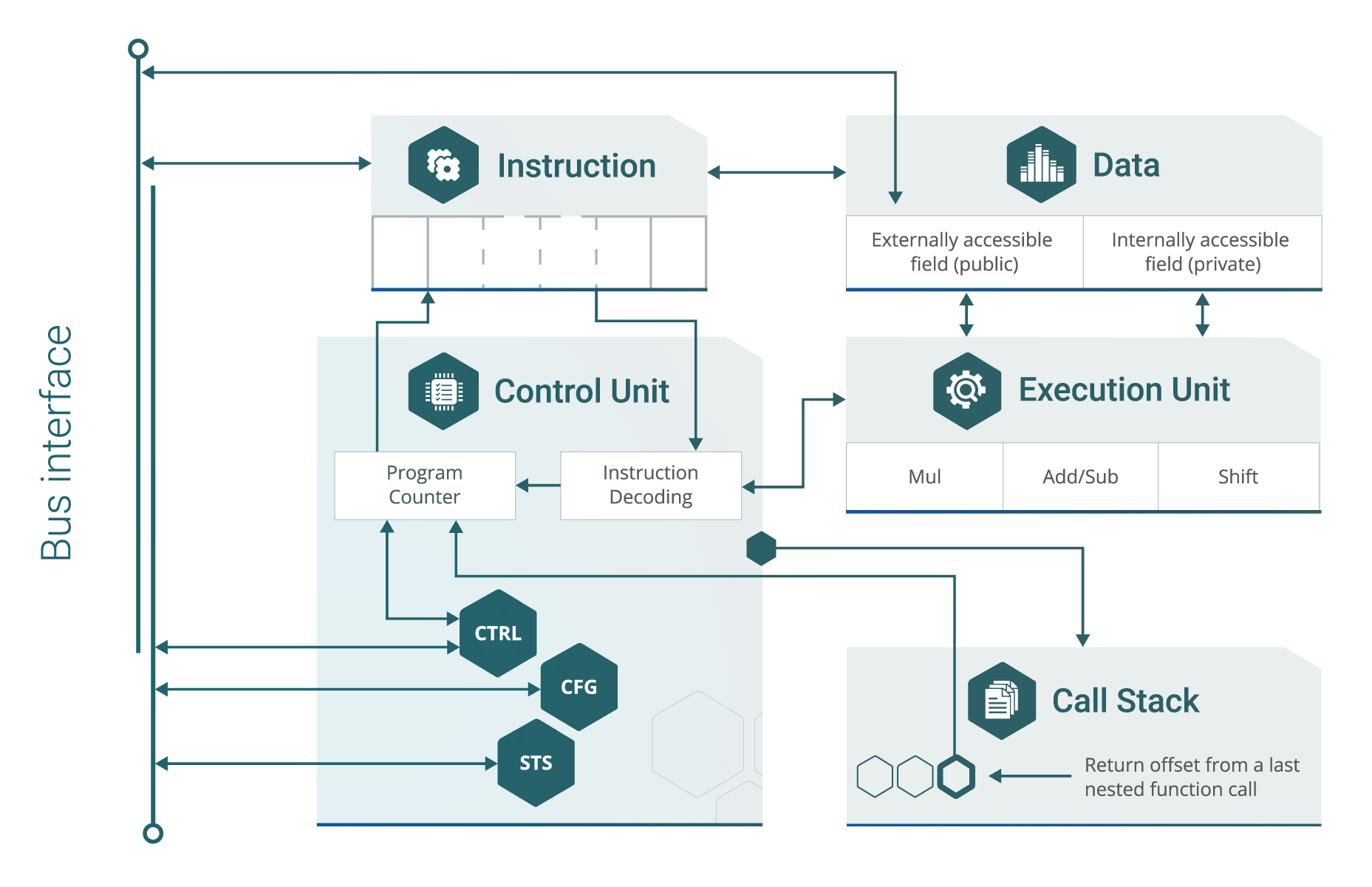
Block Diagram